The issue started when Florida-based BLU Products admitted that some of its handsets made in China and used in the US were transmitting sensitive user information back to a server in Shanghai, China.
Samuel Ohev-Zion, the chief executive of the Florida-based BLU Products, told the New York Times: “It was obviously something that we were not aware of. We moved very quickly to correct it and requested all data be destroyed.”
iTWire's Sam Varghese reported on this and mentioned that ADUPS also provided software to ZTE and Huawei. ZTE has since stated, “No handsets sold in the US have ADUPS.” Huawei stated that it takes its customers' privacy and security seriously, and it works diligently to safeguard that privacy and security. It said the company mentioned in this report was not on its list of approved suppliers, and it had never conducted business with them.
|
|
According to the New York Times, American authorities say it is not clear whether this represents secretive data mining for advertising purposes or a Chinese government effort to collect intelligence.
ADUPS says it is blameless too. The software (firmware updater) was written long ago at the request of an unidentified Chinese manufacturer that wanted the ability to store call logs, text messages, and other data for customer support. “Adups is just there to provide functionality that the phone distributor asked for,” said Lily Lim, a lawyer in Palo Alto, Calif., who represents ADUPS.
ADUPS will not release a list of affected brands or handsets. The software continues to be used unchanged in China and many other countries – it has just been fixed for phones sold in the US, about 120,000 BLU handsets.
Kryptowire discovered the issue and has a great article here showing what is collected. It is way more than what could be reasonably expected.
But this is not the first time similar things have happened.
A few years ago every bit of Chinese technology was suspect – Huawei and others paid dearly for the campaigns waged against them.
In 2014, Chinese smartphone manufacturer Xiaomi was accused of sending user data to China. Lenovo — like many other device manufacturers — installed “Superfish bloatware” on devices before shipping to inject advertisements into browsers but there were security vulnerabilities within the software that enabled attackers to read encrypted browsing data including passwords and other sensitive items.
Flashpoint summarises what many are wondering:
Despite the incentive against abusing their supply-chain dominance for intelligence purposes, the Chinese government possesses considerable powers to compel companies and manufacturers to do so. The recent passing of China’s new Cybersecurity Law only expands these powers.
However, these risks are not exclusive to Chinese-based manufacturers. Many non-Chinese firms manufacture and/or assemble their components and devices in the PRC; hence, the threat to the supply chain remains even if using non-Chinese devices. As such, malicious hardware, firmware, or software could be injected at any stage of the process, although the ease with which this is done may differ considerably.
What can you do?
The spyware is likely installed on “low cost” smartphones, especially those that are white labelled by telcos, and third parties or those who use advertising to reduce handset costs.
ADUPS says on its website it has a worldwide presence with more than 700 million active users, and that its firmware is integrated into “more than 400 leading mobile operators, semiconductor vendors and device manufacturers spanning from wearable and mobile devices to cars and televisions".
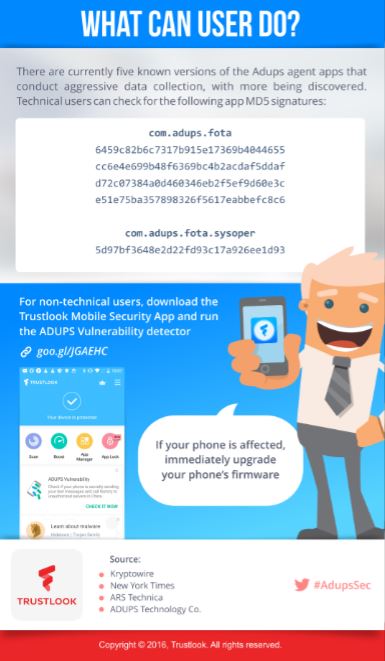
Trustlook, a next-generation mobile device security company, has released a new feature in its Trustlook Mobile Security app that identifies the presence of rogue firmware from ADUPS.
The Trustlook Mobile Security app can be download for free from Google Play. It currently checks for all known versions of the ADUPS system apps that conduct aggressive data collection, with more being added as they are discovered.